2002 was the year I faced the challenge of implementing my first Security Operations Center (SOC). Its purpose was to manage security infrastructures such as Firewalls, VPN, IDS and Proxy to support customers in the management and operation of their security architecture.
In 2006, in a Big Four, I proposed the implementation of a SOC more oriented to monitoring, incident management and the analysis of different sources of security events, through correlation tools in order to reduce false positives. In the end, this tool called SIEM became the nerve center of the cybersecurity operation.
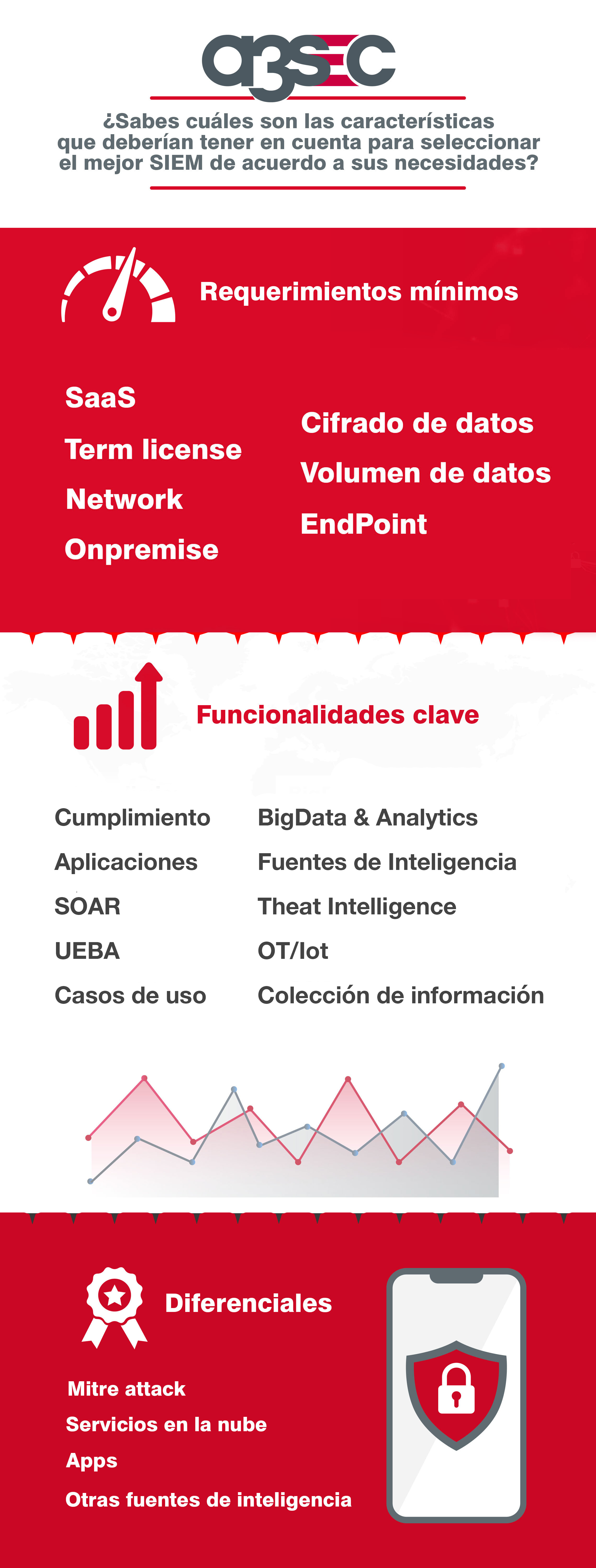
Some of the concerns raised by security officers (CISOs) of organizations are focused on the characteristics that should be taken into account in order to select the best SIEM according to their needs. For this purpose, A3Sec Group has developed an analysis based on Garner's magic quadrant in order to establish the minimum characteristics of a SIEM, the key functionalities and their differentials.
Next, I will list the minimum requirements, mandatory functionalities that SIEM systems must have, their absence leaves out of competition in the current environment; key functionalities, which refer to how SIEMs are constituted in order to fulfill their purpose at the moment; and their differences, which are the unique and innovative characteristics that the market leaders have.
These are the minimum requirements that a SIEM solution must have in order to meet the established objective:
- SaaS: it is a Cloud Native solution with scalability and easy deployment capabilities.
- Onpremise: it is a solution for local implementation in virtual machines or physical machines.
- Data Encryption (Integrity and Confidentiality): it is a solution that protects the integrity of the data from the origin, in its processing and in backup. It includes obfuscation capabilities.
- Term License: refers to the terms established in the license. All technological tools have migrated their licensing models on an annual basis, based on their financial orientation.
- Data Volume License: currently the most widely used licensing model in SIEM solutions. The sizing is supported by events per second (EPS) or amount of data indexed per day.
- Network: integration and exploitation of network events.
- EndPoint: integration and exploitation of host events.
The key functionalities of SIEM systems are listed below:
- UEBA: refers to the analytics of anomalous user and equipment behavior, which has become an important capability within SIEMs, in order to reduce the number of possible alarms.
- SOAR: security orchestration and automation systems that support incident response.
- BigData & Analytics: BigData & Analytics:current SIEM solutions must rely on BigData technologies and have the ability to apply both determining and machine learning models in order to detect the unknown.
- Own intelligence sources: this functionality is available by generating insights through an ecosystem or an internal research team, both indicators of compromise (IoC) and indicators of attack (IoA).
- Threat Intelligence Module: these sectionals or modules support the management of multiple intelligence sources, helping in the update of new IoC and eliminating those that no longer generate a risk for organizations.
- Compliance: modules that help identify the effectiveness of controls aligned with different standards, laws and regulations. Depending on the type of sector, it must have the corresponding alignment and use cases for: HIPAA (Health Sector Information Security), PCI-DSS (Cardholder Data Protection), GDPR (Personal Data Protection) and NIST 800-53 (Security and Privacy Controls for Government Agencies).
- Applications: is the integration with logs of applications such as: Email, ERP, MainFrames, among others.
- OT/IoT: is the integration with operation networks and the Internet of Things.
- Capacity for parser development: it is a functionality for the integration of new information sources with diverse structures.
- Capacity for use case development: it is used for the development of the organization's own use cases.
And finally, I share with you the technical functionalities, which we believe have become differential and innovative in today's SIEM systems:
- Mitre Attack: In order to reduce alert weariness, both timelines and attack frameworks have been applied. The best positioned in the sector is Mitre Attack, all use cases have labels of the attackers' techniques, tactics and procedures.
- Other intelligence sources: it is essential not to be closed to own intelligence sources, but to have the ability to process sources such as TAXII or STIX.
- Cloud services: migration to the cloud is a reality. SIEM platforms must have the ability to integrate, through APIs, information sources from cloud services and develop security use cases for these services. Some of the key integrations are: AWS, AZURE, Google Cloud, SalesForce, Office365 and GSuite.
- Apps: developing an ecosystem of integration of different solutions directly supported by manufacturers helps the solution to evolve. In the Apps portals, manufacturers such as: CISCO, Microsoft, Amazon, Google, CheckPoint, IBM, McAfee and SAP, publish applications to make the most of their logs in the new generation SIEMs.
However, there are some functionalities that are rare in SIEM systems, but some factories show them as an advantage. It must be determined if they are really an advantage or if, on the contrary, they do not contribute to the organization's objective in terms of safety. I share some of them below:
- Vulnerabilities: some solutions have integrated vulnerability analysis systems. They generate the scan schedule and structure the results, showing trends and changes through ticket management. The results can be processed by SIEM BigData and can be further enriched with a multitude of use cases of particular attacks by exploiting such control flaws.
- Appliance: the acquisition of hardware and assets in technology projects is decreasing due to the trend of migrating to the cloud and Cloud Native platforms. Some government agencies in Latin America continue to see the need to acquire hardware.
- Common Criteria EAL 3+: some security controls have EAL 4+ levels in SIEM, being an internal platform that is supported with medium-high levels of operating system security. However, depending on the security level of the organization and the type of data to be processed, this type of requirement must be validated.
- CMDB: having a database of configuration items helps to have security operation tasks. Some examples are: performing passive vulnerability analysis by validating the version of installed software packages and vulnerability databases and identifying unauthorized changes in hardware or software. Although many of these activities are identified by user events or actions, most SIEMs are natively integrated with such databases.
As a member of the A3Sec team, I add that we are concerned about updating our tools according to the technological advancements in the market and about adapting to the new cybersecurity environment, in order to share our knowledge and experience to our customers with different requirements and needs, focused on their type of organization and sectorial reality.