The Healthcare Sector is suffering the biggest cyber-attacks taking advantage of the current pandemic caused by Covid-19:
- More than 150 countries
- More than 230k endpoints involved.
- Significant impact on healthcare infrastructure: computers, MRI scanners, refrigerators, etc.
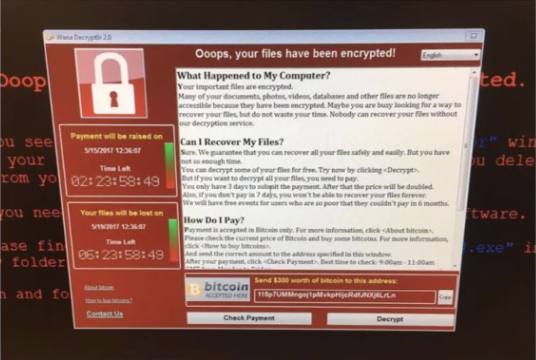
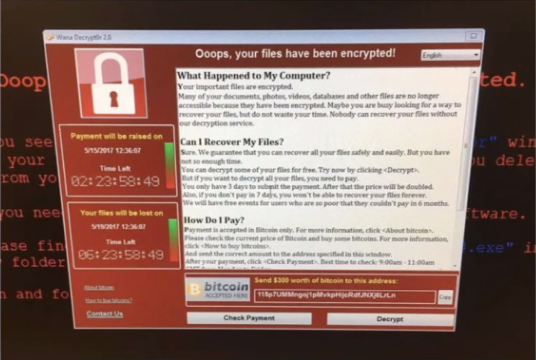
Without going any further, on March 23 it was published the existence of a cyberattack considered very dangerous against Spanish hospitals in the middle of the Covid-19 crisis, it is the "NetWalker" program, a ransomware (type of cyberattack that blocks the victim's computer systems and asks for a ransom in exchange for the key to release them) which, as reported by police sources, would be the basis of an offensive whose "targets would be mainly health workers and agencies".
The ransomware was detected by cybersecurity agencies and, according to José Ángel González, Deputy Director of Operations (DAO) of the National Police, it has the capacity to "break the entire computer system of hospitals". The DAO has specified that it is "very dangerous" malware and is transmitted via email, so he has asked healthcare professionals to be extremely cautious when handling this tool.
Its mass distribution has not yet begun in Spain, according to police sources, but "given the health emergency situation in which we find ourselves", a successful cyberattack with this ransomware on a healthcare center "would have devastating consequences".
In April 2019, a team of security researchers developed a new malware capable of altering the results of our X-rays. The malicious tomographic scanner and MRI software, is capable of making cancerous tumors appear on our medical tests, confusing medical professionals. Infiltration into hospital systems is the order of the day, and manipulation of clinical systems has already arrived, with the obvious danger that this entails.
Basically, the Health Sector faces two problem
-
- The data it handles.
This is the most targeted sector because it is one of the ones that generates the most money. And not only because of the profits that can be obtained from the extortion of health institutions, but also because some buyers are willing to pay large sums for the purchase of digital medical records, which have a value on the black market that amounts to 50 times that of credit card data. One of the problems with the hacking of medical data, compared to that of financial data, is that while consumers can immediately detect when a bank account has been compromised, it is more difficult to detect in the medical field, often these data breaches are never discovered, which is a big advantage over credit card theft, which is quickly cancelled by banks when the fraud is detected. - Very diverse information systems infrastructure.
And often with outdated, deeply deployed and difficult to replace devices, many of them already unsupported by manufacturers that require a great deal of complexity to keep them updated for well-known vulnerabilities.
- The data it handles.

Forecasts in the field of Cybersecurity for 2020 already warned about the uncertainties of the Sector, forecasts overwhelmed by the impact of the current healthcare crisis:
- Interest in medical records on the 'Dark Web' will grow. Research on underground forums reveals that such records are sometimes even more expensive than credit card information. This also opens up new possibilities for fraud: with someone's medical data it is easier to defraud the patient or their relatives.
- Access to internal patient information makes it possible not only to steal but also to modify records. This can lead to targeted attacks against individuals in order to modify diagnoses.
- The number of attacks on devices in medical facilities in countries that have just begun the process of digitization in the field of medical services will increase significantly in the coming year. We foresee the emergence of ransomware attacks targeting hospitals in developing countries. Medical institutions are becoming industrial infrastructures. Loss of access to internal data (e.g., patients' digital records) or internal resources (e.g., connected medical equipment within a hospital) can slow down patient diagnosis and even disrupt emergency help.
- There will be more and more targeted attacks against medical research institutes and pharmaceutical companies conducting innovative research. Medical research is extremely expensive and some APT groups that specialize in intellectual property theft will attack these institutions more frequently in 2020.
- Fortunately, we have never seen attacks on implanted medical devices (e.g. neurostimulators). But this is only a matter of time, as there are numerous security vulnerabilities in these devices. The creation of centralized networks of portable and implanted medical devices (as in the case of cardiostimulators) will lead to the emergence of a new threat: a single point of entry to attack all patients using such devices.
Source: Cybersecurity of connected healthcare 2020: Overview and predictions. Kaspersky
Need to implement an effective protection strategy? Talk to one of our consultants

Therefore, strategic decision-making on the implementation of cybersecurity systems in the healthcare sector is crucial. The EU Cybersecurity Agency, ENISA, published last February 24 a series of recommendations to improve hospitals' protection against cyber attacks:
- Involvement of the IT department in the purchasing and procurement processes from the outset so that security is taken into account and it can make an analysis of how the technology adapts to the existing network and assess whether additional measures need to be taken.
- Implementation of a vulnerability identification and management process, so that vulnerabilities can be managed throughout the lifecycle of all devices.
- Develop a hardware and software update policy. At this point, IT teams are advised to determine the most appropriate time to apply patches to each network segment, as well as to determine alternative solutions, such as segmentation for machines that cannot be patched.
- Improve wireless network security controls to prevent unauthorized access, as well as establish testing policies. Hospitals acquiring new IT products should establish a minimum set of security tests to be performed on new devices added to networks. These would have to include penetration tests to take into account how hackers may attempt to break into systems.
- Development of Continuity Plans that allow key services to continue operating in the event of an incident. It is essential for a hospital to be able to transfer information and data with other centers, but in the event of a cyberattack or system failure, there should be a backup plan.
- Encryption of sensitive personal data, whether at rest or in transit.
- Maintain and manage system logs, which will ensure that in the event of a compromise, it will be easier to trace what happened and how the attackers gained access to the system, as well as to assess what information has been compromised.
Do you want to implement this type of protection in your organization?