When we talk about the Attack Surface, we refer to all the potential vulnerabilities that may exist throughout the organization, at any level. Any weak point in the structure can be a gateway for potential attackers, and therefore, it is necessary to have a comprehensive cybersecurity solution.
The challenges for organizations seeking to reduce their Attack Surface.
The Attack Surface is the sum of the different 'attack vectors'. When we talk about vectors in this context we are talking about malicious code such as viruses or Trojans, among others, that use vulnerabilities in a system or structure to infect and propagate. Due to the increase of digitalization in all types of companies and organizations, there are more and more elements exposed to an attack that all it needs to be successful is a backdoor, a vulnerability or a code error to be inside the system. To prepare for and prevent this type of attack there are three factors that will help us to understand and visualize the attack surface.
- The complete mapping of all devices, routes and networks in the organization.
- Finding vulnerabilities that are likely to lead to an attack.
- Having visibility into what is published about the organization on the Internet.
These three points are fundamental when conducting a cybersecurity audit with the objective of reducing the Attack Surface. Generally, the keys to successful reduction are: reducing the number of unauthorized user accesses, managing vulnerabilities efficiently, having the ability to respond in a timely manner to the different threats in cyberspace.
What elements are included in the Attack Surface of a company?
With the advent of the Internet of Things, organizations have multiplied the number of devices susceptible to attack. With hundreds of elements connected simultaneously on the same network, it is relatively easy to find a vulnerability in one of them, so spending time mapping and monitoring the entire structure is necessary to ensure an acceptable level of security. There are three categories into which the Attack Surface can be divided:
- The network attack surface
- Software attack surface
- The hardware attack surface

Every device connected to the network is a potential point of attack. You can reduce the Attack Surface of the network by closing ports that are unnecessarily open and limiting the services that are available to unauthorized users, including Internet access in general, with methods such as MAC address filtering. It is about reducing attack vectors to limit software exposure by simply blocking user access to certain programs or privileges within the system. If I cannot install programs without authorization, I am less likely to install a program with malicious code within the system.
When we talk about software we talk about code and any element that is running code can have vulnerabilities that can be exploited. The idea is to minimize the amount of running code so that malware has a harder time using multiple exploits.
When thinking about the Attack Surface we don't often think that a physical attack against the organization's equipment is also part of the risk. There are many security flaws that organizations do not take into account, such as keeping passwords in plain sight, discarding old computers or hard drives, etc. To reduce the Attack Surface, it is also necessary to have a protocol for physical risks.
Comprehensive solution to reduce the Attack Surface
When dealing with the reduction of the Attack Surface, it is necessary to approach it in a comprehensive manner, with a solution that guarantees that the risk will be minimized.
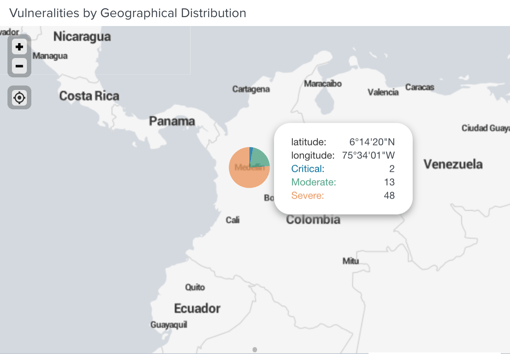 At A3Sec we provide the "Attack Surface" service with the Code solutions, Infrastructure, Network and Passive Vulnerability Management.
At A3Sec we provide the "Attack Surface" service with the Code solutions, Infrastructure, Network and Passive Vulnerability Management.
We provide companies with the necessary technology for the constant identification of vulnerabilities on infrastructure, applications and services. How? Through:
- Vulnerability analysis tools specialized in VM and WAS.
- Open sources and intelligence sources
We provide our experience and knowledge for the integration of technologies specialized in the detection of vulnerabilities and threats, with a big data platform where all the analysis of such information converges, through dashboards and management KPIs, which allow the organization to have control over its infrastructure, manage its vulnerabilities in a timely manner and facilitate better decision making.









