How much importance do companies attach to cybersecurity? Although we are in an era where digital security is vital, less than 40% of companies consider cybersecurity to be of high importance. Could this become a problem?
The security of end-to-end monitoring in your enterprise.
There is a problem with how most companies perceive the importance of cybersecurity to their business. Not only because they underestimate the economic impact that an attack of this type can have, but also because in the event of an attack, they have neither the measures to try to counteract it nor the tools to monitor their systems in order to contain and prevent future attacks. And that is the key to cybersecurity in companies: monitoring.
The monitoring consists of collecting all the information from the company's devices and systems in order to detect errors, vulnerabilities or attacks with the aim of taking measures in a fast and effective way. Given the large amount of data that companies handle, it is necessary to have specific tools that are capable not only of processing all this data, but also of interpreting it so that the cybersecurity team can take action. Monitoring is a very necessary action that should not be limited only to large corporations, since SMEs are equally exposed to attacks and are just as vulnerable.
According to several studies, four out of ten organizations have suffered security breaches in the last two years and the main barrier these companies face is the lack of sufficient resources to deal with an effective defense.
Most of these security problems can be prevented with monitoring tools as they allow us to control everything that is happening in our organization and to be able to apply measures in a preventive and reactive way, in real time.
Interpretation of monitoring data: the main challenge
The data generated by machines is often displayed in a seemingly chaotic way, requires a lot of processing to interpret and it is usually difficult to know what we need to look for to get relevant information. The goal of data monitoring processes is not only to extract data, but to be able to process and interpret it. The key is to have a tool that allows you to operate with it at all the necessary levels:
Single platform - A system that provides useful data to any member of the organization from one place.
Performance and scalability - The volume of data generated by some companies is gigantic and the solution must be able to process it while being scalable and reliable for the organization.
Open ecosystem - Allowing the participation of different partners and developers and complemented by a good number of applications that allow customization of the solution.
Hybrid system - Different companies have different needs, so ideally the tool should be able to operate both on-premise and in the cloud.
Splunk: security monitoring solution
In order to effectively monitor all the company's processes, it is important to have two elements: adequate tools and a prepared team.
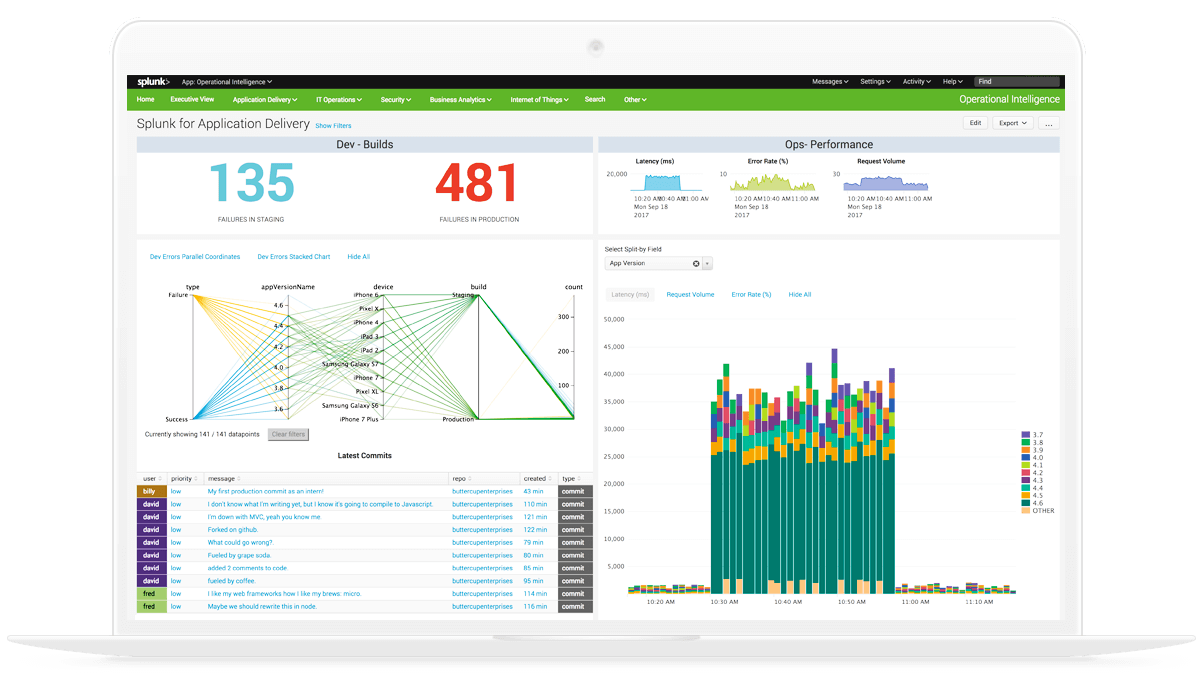
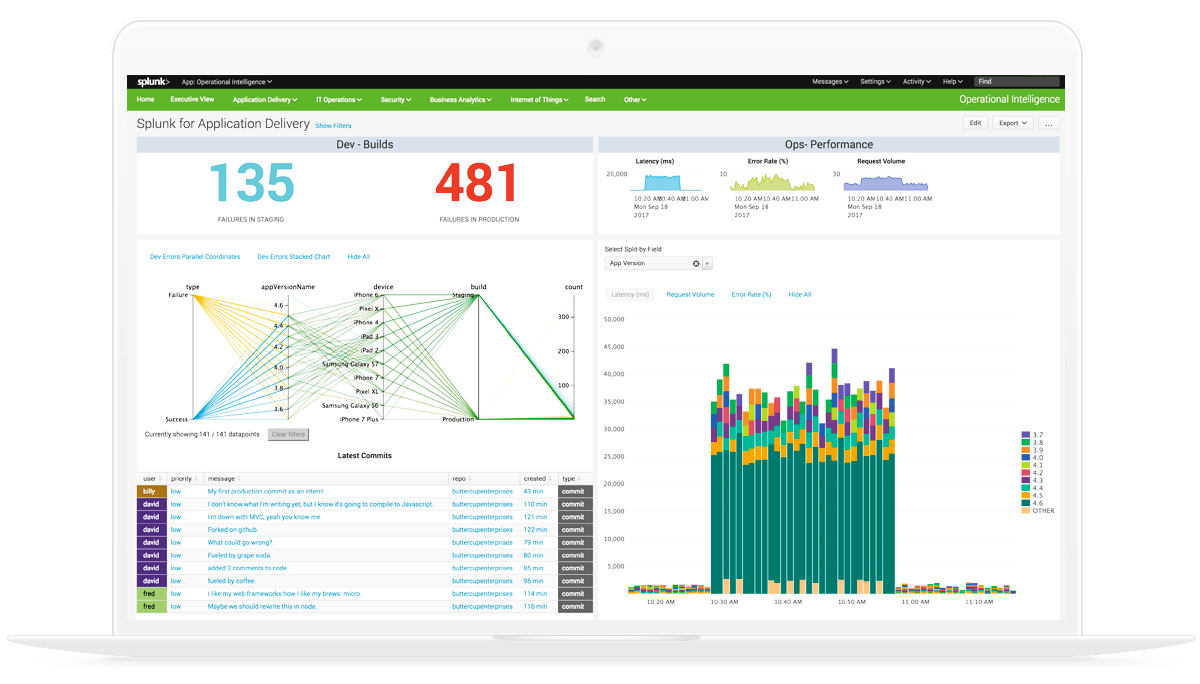
Splunk is the world's leading SIEM (Security Information & Event Management) solution (according to a Gartner report). This solution makes it possible to monitor and analyze all the company's Big Data (in applications, systems and infrastructures) through a web interface. All this information is interpreted and captured in a repository through graphs, alerts and dashboards with clear and useful information for decision making.
Where does all this information come from? Machine data is the information generated by any connected device or system: GPS, RFID tags, servers, applications, phones, computers, data centers, devices, etc. A tool like Splunk is able to read, process and interpret all the Big Data from these devices and produce relevant information for the company. If we do not have a solution of this type, the amount of data together with the difference in formats, languages and structures, would make it impossible to interpret. To give value to all this information, Splunk relies on five main functions:
Index - The part that collects data from all sources and processes it, keeping constant identification of all events and storing them for later search.
Search & Investigate - Splunk's search engine allows you to find events, allowing you to analyze and run statistics.
Add knowledge - With this function you can manually add data to help with the interpretation of data, allowing you to classify, normalize and save reports.
Monitor & Alert - The monitoring section allows you to identify problems and apply solutions before an attack impacts clients and services. In this functionality, alerts can be configured to set up automatic responses to certain events.
Report & Analyze - Creation of reports and visualizations for decision making.
Although Splunk is a very powerful tool, its management requires an expert team that can take charge of the management of such an important process such as security monitoring, with tools such as Splunk. In order to achieve the best results and meet these objectives, there are specialized companies such as A3Sec, with a customer-oriented approach and formed by a multidisciplinary team of professionals, whose expertise in the field of cybersecurity in general and Splunk in particular, can be decisive when adopting this solution.
A3Sec turns DATA into the engine of the business growth of organizations as it manages large volumes of data through its procedures and protocols, using the best existing tools and betting on innovation in each of its actions. In the field of monitoring and thanks to tools such as Splunk, A3Sec also offers an accessible service to small and medium-sized companies without renouncing the technology used by the largest ones.
Monitoring your company and its cyber security
Monitoring is one of the cornerstones of protection in the field of cybersecurity. It does not matter how many preventive measures are taken to counter an attack if the company's data are not interpreted correctly, since decisions will not be based on objective and real information. Many companies fail precisely in the part of monitoring and interpreting data and, therefore, leave vulnerabilities uncovered. A solution like Splunk with a high-level team like A3Sec's is a guarantee of quality in the field of cybersecurity