TABLE OF CONTENTS - INDEX
- Introduction to SIEM: How has SIEM evolved?
- Gartner's Magic Quadrant
- Essential elements of a SIEM
- Importance of Threat Hunting in a SIEM
- Know the perfect SIEM for you
- Sizing the costs of a SIEM according to your organization.
- Future of the SIEM: What does it need to remain relevant?
- A3Sec for anti-fragile models
- Work with us
Introduction to SIEM: How has SIEM evolved?
In its formalization process, the SIEM was considered a log manager, a regulatory compliance tool for: event correlation, active response and endpoint security.
The technological environment where the elements that feed the SIEM are implemented has changed enormously. SIEM has gone through Next-Generation SIEM, Security Analytics and is now an MDR service.
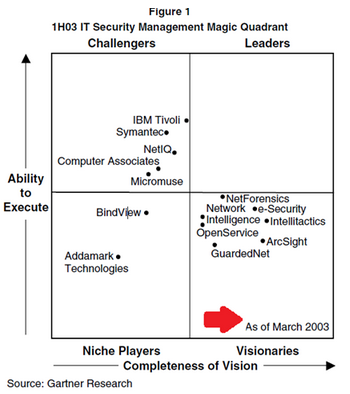
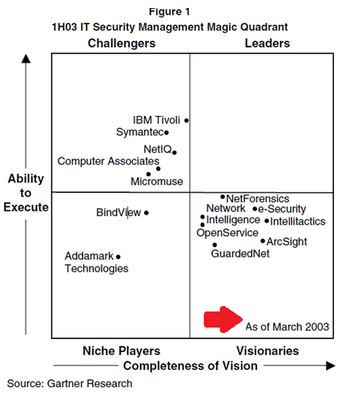
Gartner's magic quadrant
As we have seen, the origin of SIEM is to be found in Gartner's magic quadrant.
Although the magic quadrants have always been very important for the inclusion of criteria such as pricing, marketing, sales coverage, vertical strategies, innovation, there are some technical elements that can be extracted in order to compare solutions.
SIEM must-haves
Gartner identifies ten critical capabilities for a SIEM that they weight according to importance for basic monitoring and complex monitoring, as well as advanced threat detection. Then it's time to select the SIEM that best fits your business.
Why choose this SIEM and why not another? Does it really cover the features of a SIEM? Does it help meet the needs of my business? Is it qualified and does it meet the necessary security goodness to be a mature SIEM?
Importance of Threat Hunting in a SIEM
The use of technological tools such as Threat Hunting supports the maturity of a SIEM.
The objective of threat hunting is to build knowledge that helps us to make our detection and response processes more effective by covering the risks presented in the security operation. Now, let's see what tasks the threat hunter has.
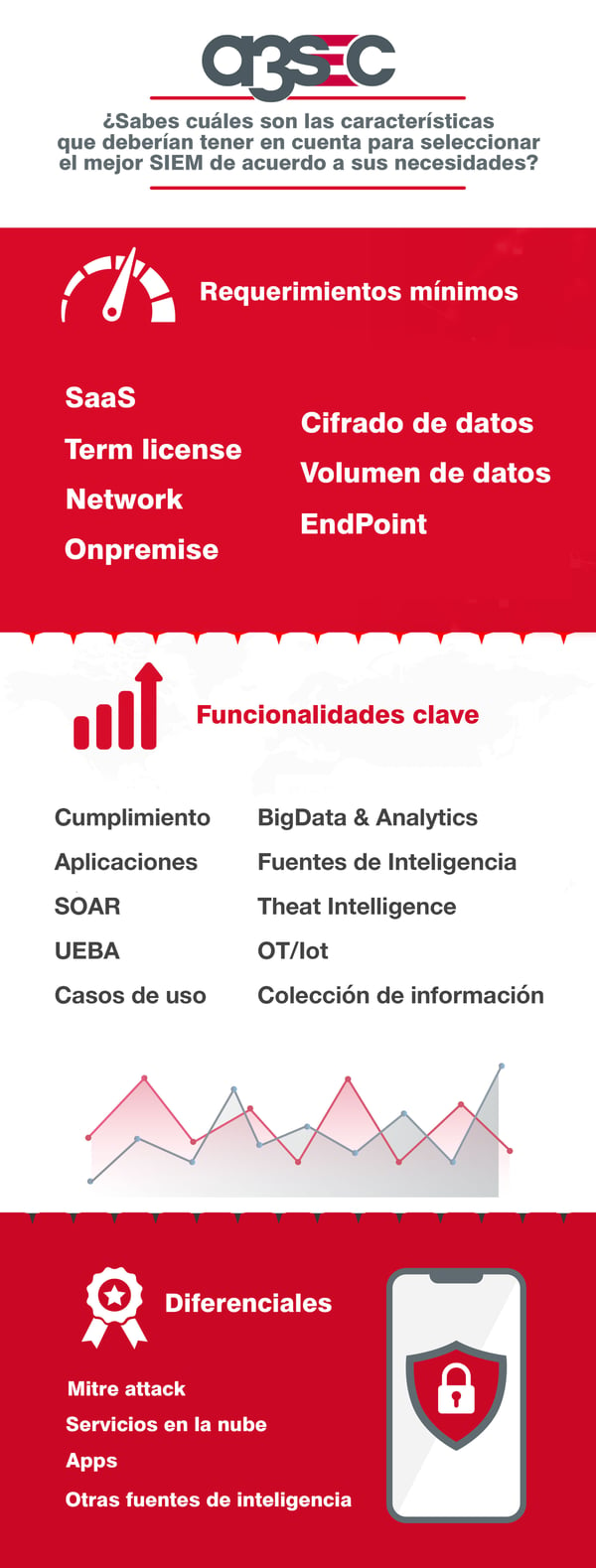
Know the perfect SIEM for you
Taking into account the capabilities of a SIEM and based on Gartner's magic quadrant, A3Sec Group has developed an interactive tool that allows you to define, from the minimum features of a SIEM, the key functionalities and their differences, which SIEM best suits your particular needs.
- Minimum requirements: mandatory functionalities that SIEM systems must have.
- Key functionalities: how SIEMs are constituted to fulfill their purpose today.
- Differentials: unique and novel features that market leaders have.
Estimating the costs of a SIEM for your organization
At A3Sec we have identified four key concerns that our clients frequently wish to resolve in order to make the best decision regarding the acquisition of a SIEM system for their organizations: problems, solution, project risks and costs.
To offer you clarity and the possibility of comparing different SIEM proposals, we have developed an interactive tool where, based on a series of key elements, we offer you an estimate of the total cost of a SIEM solution according to your organization.
Learn how our interactive tool helps you select the best SIEM for your organization.
Future of the SIEM: What does it need to remain relevant in the market?
Below, we will share with you some fundamental points for a SIEM to remain relevant in the market.
The future of the SIEM lies in the ability of organizations to better structure their information. With the advent of digital transformation, hybrid infrastructures (cloud-onsite) are appearing and the SIEM must be prepared for updates and new tools.
Más allá de la resiliencia: Modelos de Ciberseguridad Antifrágiles
A3Sec por los modelos antifrágiles
En definitiva, en A3Sec buscamos incansablemente proteger el Conocimiento para evolucionar con nuestros clientes a modelos antifrágiles de ciberseguridad.
Descubre la diferencia entre los modelos de gestión de riesgo resilientes y los antifrágiles. ¿Por qué antifrágiles en lugar de resilientes?
Más allá de la resiliencia: Modelos de Ciberseguridad Antifrágiles
A3Sec stands firmly for anti-fragile models
In short, at A3Sec we tirelessly seek to protect Knowledge in order to evolve with our customers towards anti-fragile cybersecurity models.
Discover the difference between resilient and anti-fragile risk management models. Why anti-fragile instead of resilient?
Beyond Resilience: Anti-Fragile Cybersecurity Models
Work with us
Want to know more about SIEM? We offer integral solutions of Cybersecurity, Monitoring and Business Intelligence.
For more information please contact our experts.