Nowadays it is well known that it is necessary to perform within our organization, validation of security controls to face adversaries, know current threats and thus be able to know our blind spots and areas of opportunity within our organization.
Performing these validations and tests requires a great technical effort and is usually complex, difficult to replicate, in addition to the fact that managing the results can be a challenge since there is a wide spectrum of types of attacks, each with its variety of techniques and techniques.
Among the options for these validations mentioned we have the traditional and well known "Pentest" and more recently we have the concept of Adversary Emulation.
What is the Adversary Emulation?
Adversary emulation is an activity where security experts emulate how an adversary operates. The ultimate goal, of course, is to improve the organization's resilience to these techniques.
In the current ecosystem we can find different tools that can help us to perform different types of tests for Adversary Emulation.

Figure 1 : Emulation Tools
Attacker Emulation vs Pentest
Unlike traditional pentesting, the Adversary Emulation allows us to use techniques known and standardized by MITRE ATT&CK, which can be repeatable and replicable for multiple numbers of targets, easy to measure, easy to share and relatively low cost. However, a traditional pentest is the best simulation of a real attacker, but these as we know have their difficulty in replicating the techniques, in addition to the fact that they can represent high costs. It is important to clarify that one is not better than the other, but that both are necessary in the evaluation of security controls.
Finally what we are looking for is to confirm the effectiveness of the controls and detections that we have implemented within our organization, to be able to validate if what worked yesterday still works today and not miss the detection of a technique or tactic that is widely known by the community, in addition to something that is extremely important, to validate what the supplier says. "We detected that" ... "Ok, show me!"
Having explained the issue of Adversary Emulation the question arises, why not automate the whole cycle.
The answer to this question is, of course yes, since MITRE currently has its research project focused on the automation of Adversary emulation "CALDERA", which gives us the guideline that if Mitre is doing it is that we are on the right track.
MITRE CALDERA
Mitre Caldera is Mitre's original attack framework and allows operators to easily run stand-alone penetration and attack simulation exercises.
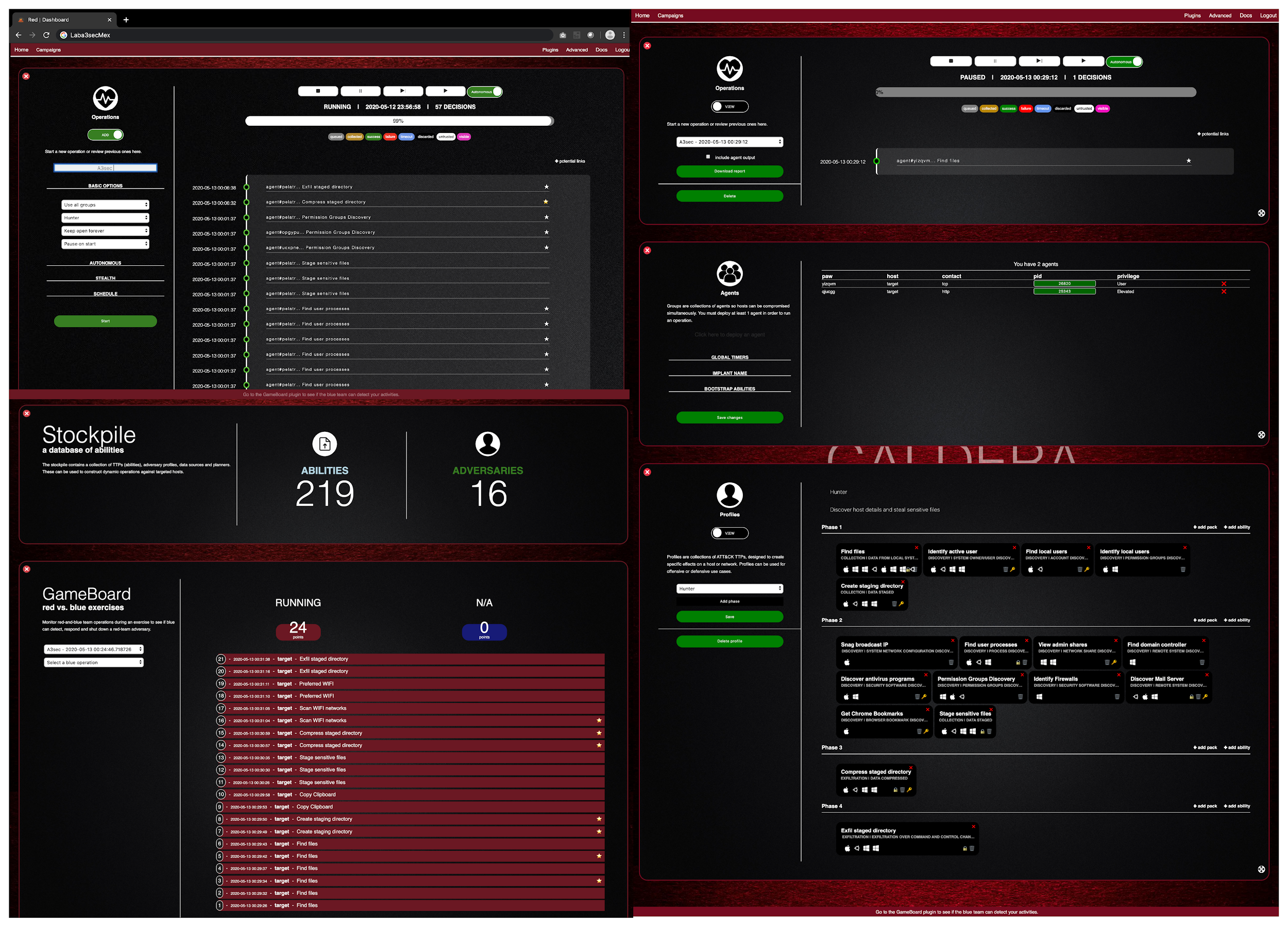 Figura 2 : Framework Caldera MITRE
Figura 2 : Framework Caldera MITRE
Automation of Attackers emulation with SOAR platform
At A3Sec we have tested the Framework and it works well, but some limitations arise as it is still a research project and is limited to the Red Team and Blue Team perspective where the results stay within the platform. It is fine from one point of view, but now with SOAR (Security Automation Orchestration & Response) type tools we can get even more scope within the management and evaluation of security controls and attack emulation.
In A3Sec we use Splunk, Phantom, Atomic Red Team - Red Canary which in turn is supported by MITRE ATT&CK and EDR Falcon Crowdstrike, in order to show the cycle of adversary emulation and validation of detections in an automated way as shown in the following image:
Solution Architecture
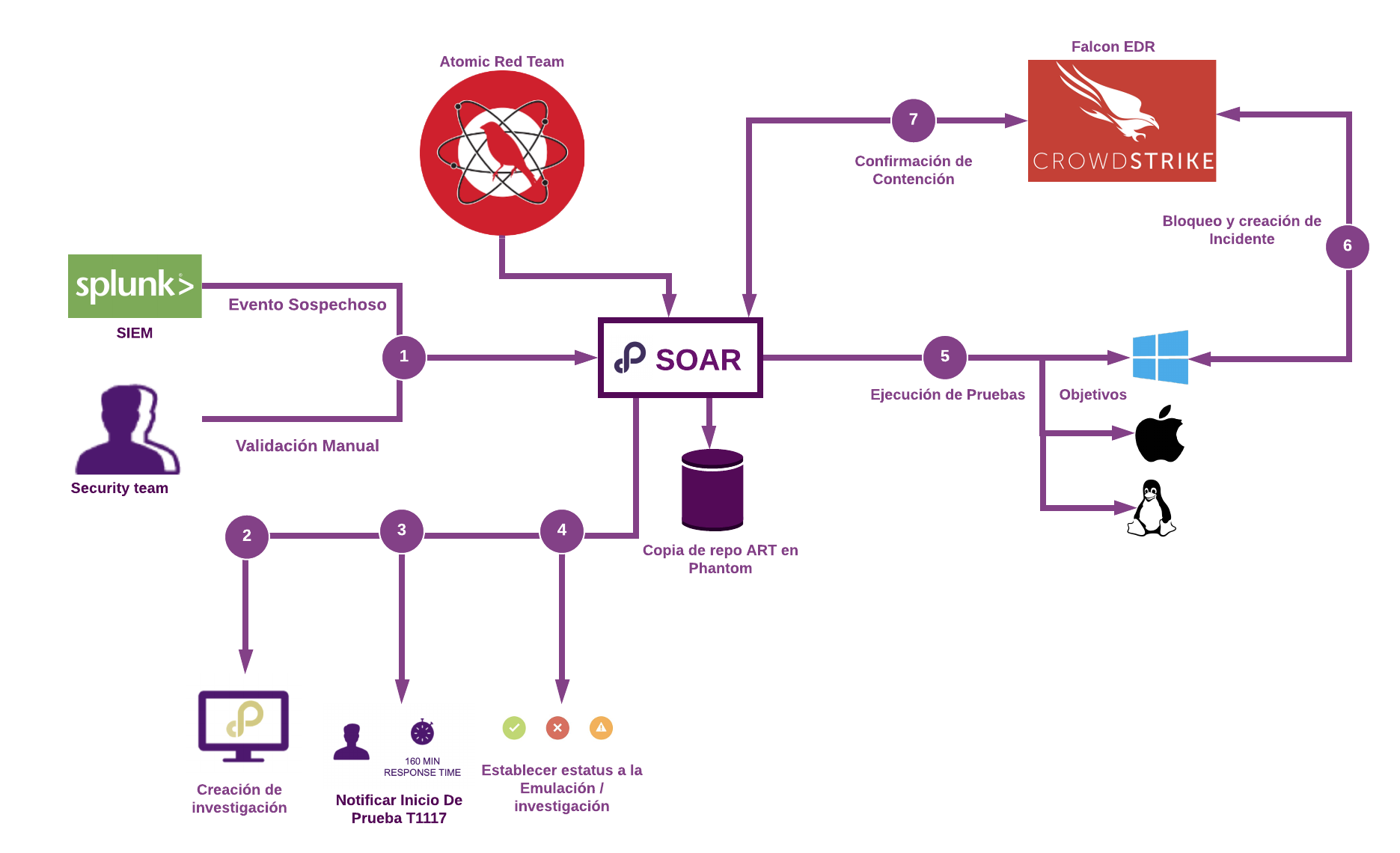 Figura 3:Diagrama de solución
Figura 3:Diagrama de solución
Do you want to implement it in your company? CONTACT US
Architecture Components
SOAR - Phantom

Phantom - SOAR Security Orchestration Automation and Responses permite a los equipos de seguridad la automatización de respuesta a incidentes. Además de ayudar a investigar, contener, erradicar y recuperarse de un evento de seguridad.
https://www.splunk.com/en_us/software/splunk-security-orchestration-and-automation.html
MITRE ATT&CK

It is a globally accessible knowledge base of adversarial tactics and techniques based on real-world observations. The ATT & CK knowledge base is used as the basis for the development of threat-specific models and methodologies in the private sector, government, and the cybersecurity security products and services
Atomic Red Team- Red Canary

Atomic Red Team are small, highly portable detection tests mapped to the MITER ATT & CK Framework. Each test is designed to map to a particular tactic. This gives defenders a highly actionable way to immediately begin testing their defenses against a broad spectrum of attacks.
EDR Endpoint Detection & Response Crowdstrike Falcon

Falcon provides continuous and comprehensive endpoint visibility spanning detection, response and forensics in order to ensure that nothing is missed and potential breaches are stopped.
https://www.crowdstrike.com/endpoint-security-products/falcon-insight-endpoint-detection-response/
SOAR and Playbooks
As mentioned above, what we are looking for is to create a complete automated flow that takes care of the complete cycle of our validation of the respective security controls. That said, the key component of the solution is the SOAR and the brain that allows us to automate all the logic is the Playbook.
In the playbook we will create all the logic of the flow of each of our tests, whether it is the validation of a complete ATP or a specific technique of our MITRE ATT&CK Matrix.
Compared to the current models of adversarial emulation, doing it with the SOAR platform will allow us through the Playbook the following points:
-
- Validate multiple techniques on multiple hosts and different Operating Systems.
- Notify the start of tests to avoid triggering alerts (false positives).
- Request test execution permissions.
- Request access to the asset owner before the start of the test.
- Contextualize the specific details of the test to the parties involved, red team, blue team, asset owners, managers, etc.
- Notify by different means, emails, slack, etc., the start and end of the test.
- Automate the sending of test results reports.
- Have a history and timeline of the executed tests.
- Assign a status, criticality, severity, etc.
- Assign the case to security analysts.
- Send results to our SIEM or other platforms for contextualization.
- Apply remediations in an automated way.
- Isolate computers identified as vulnerable after testing.
- Securely manage credentials for access to targets.
- Connect to target hosts without needing an agent or leaving a backdoor to access the hosts as Caldera does.
As shown in the list, there are many options and advantages available with SOAR, for all those reasons mentioned above, SOAR allows us to go even further in the automation of adversary emulation.
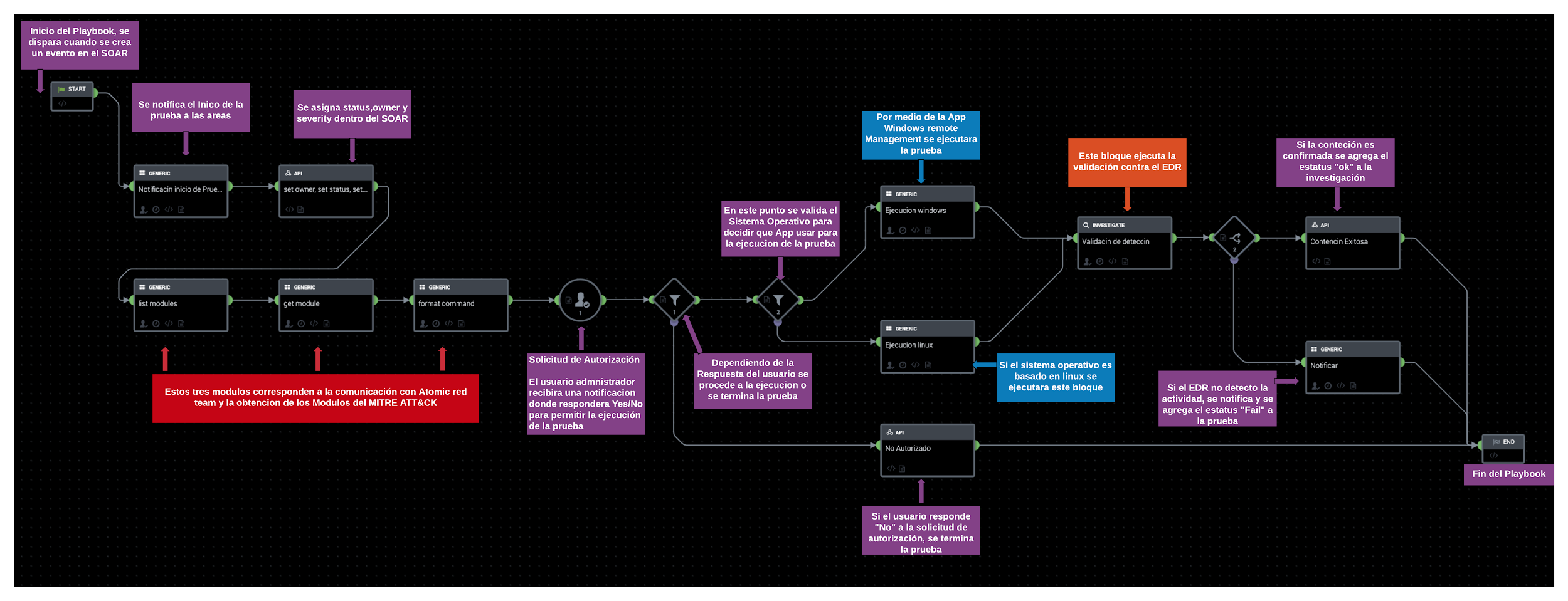 Figura 4: Virtual adversary emulation automation playbook.
Figura 4: Virtual adversary emulation automation playbook.
Do you need this type of protection? Talk to one of our Advisors
SOAR Phantom - Atomic Red Team - MITRE ATT&CK
For test automation we rely on Atomic Red Team, which is the technology that allows us to obtain the tests and the MITRE ATT&CK context for remote execution on the assets, which are part of the validation set; the advantages of this scheme is that the modules provided by Atomic Red Team are already validated and contextualized.
This type of integrations allows the use of third party frameworks to extend the capabilities of our Adversary emulation automation playbooks.
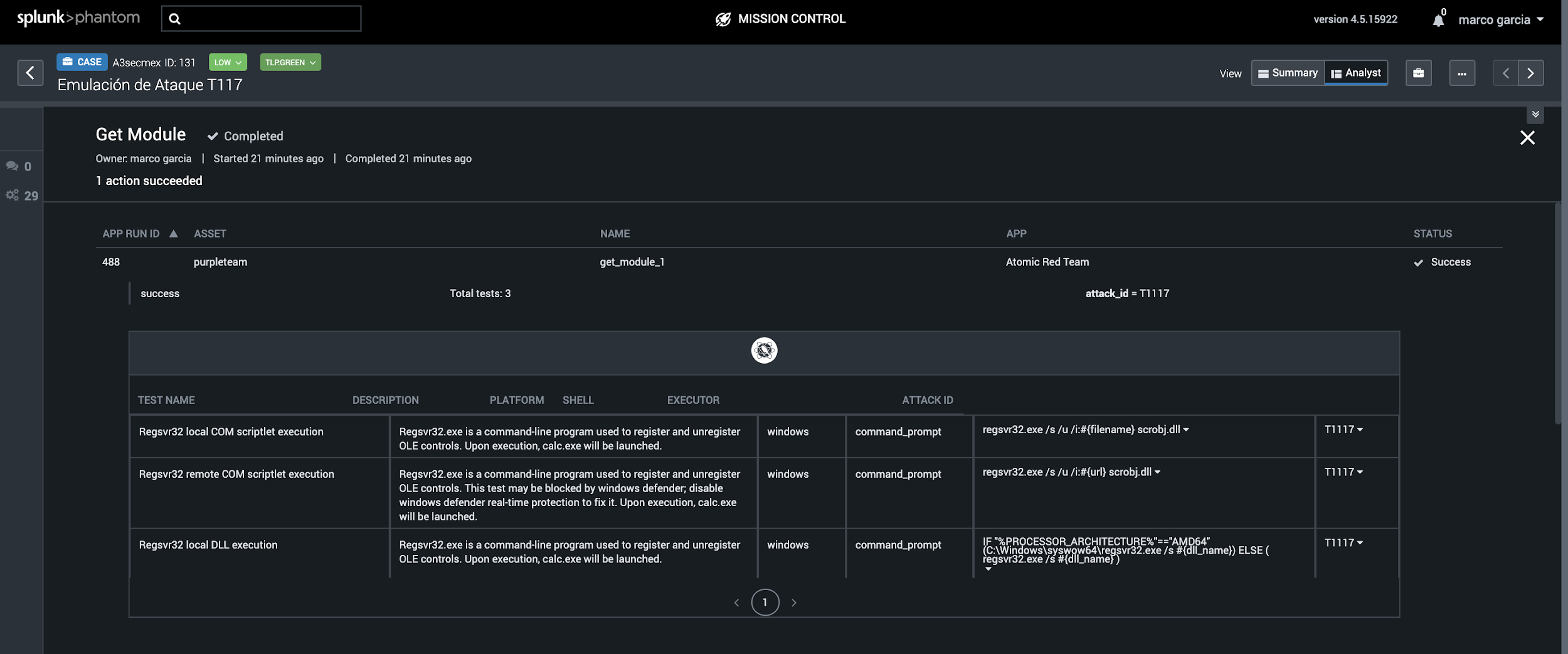 Figura 5: Atomic Red Team Phantom - Modules
Figura 5: Atomic Red Team Phantom - Modules
Detection Validation
As shown in the solution architecture, the last step in the test automation cycle is detection. If we have the ability to know which of the techniques currently used by adversaries we are able to detect and contain, we can implicitly know what our blind spots are, which is why it is not only enough to do the emulation of the attack, it is also necessary to perform detection validation.
At this point in the flow the results are binary, our defense system detects or does not detect. It is important to know that if we want to validate some technique such as T1117 Regsvr32, which is a very common technique among attackers, it can be used to perform a variety of malicious actions that are difficult to detect or block because the technique leverages a Windows component that cannot be easily disabled or restricted, and detection depends on a thorough inspection of the telemetry at the process level, our defense system must be able to detect the test and give us context of the tactics and techniques employed.
Many manufacturers claim to be able to detect based on the MITRE framework, but it is important to validate that they actually do, and with automation through SOAR it is possible to check this.
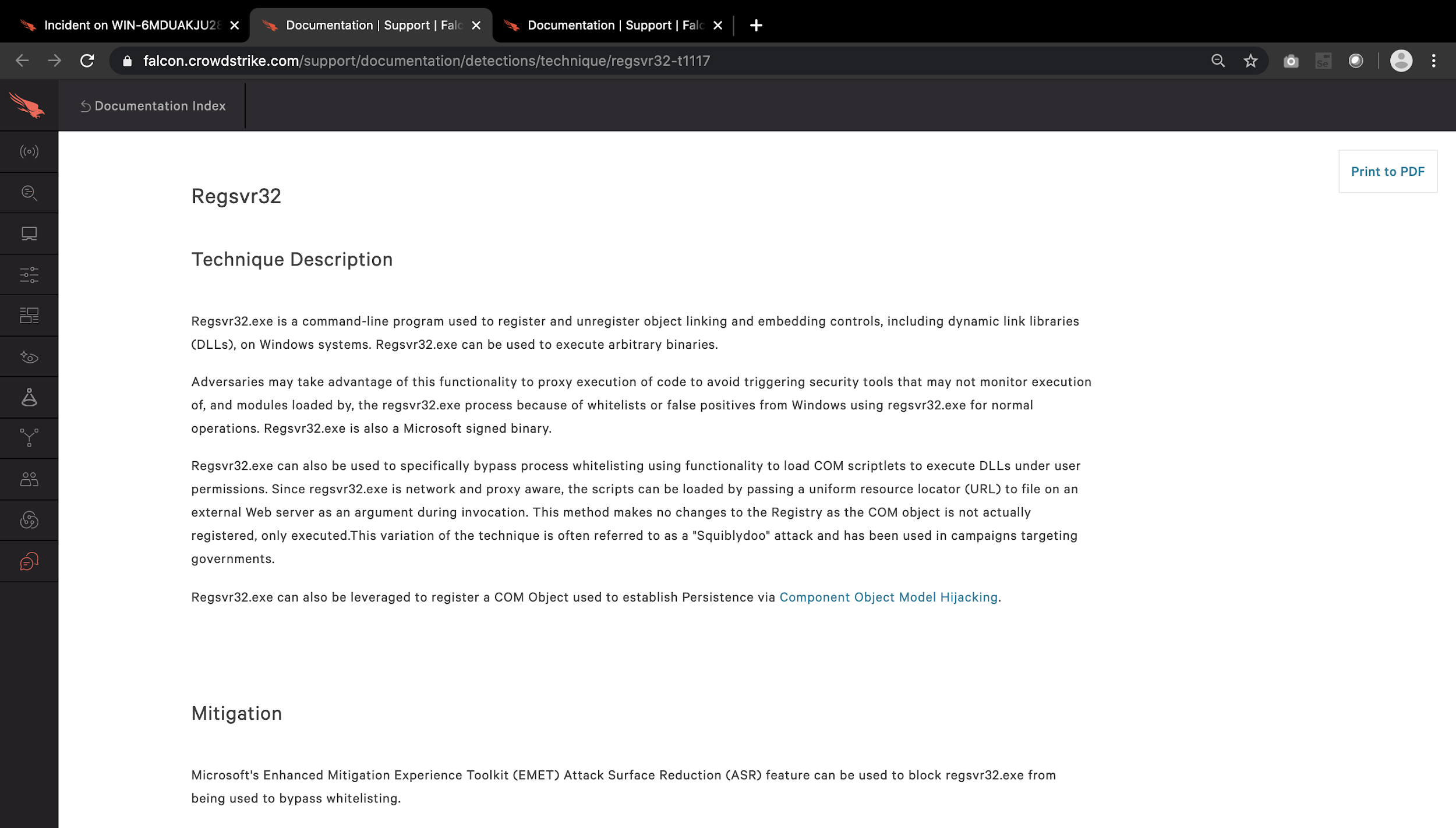 Figura 6 : Detección falcón-Descripción de técnica T1117
Figura 6 : Detección falcón-Descripción de técnica T1117
On some cases, MITRE has already tested some manufacturers and evaluated some ATPs to check the efficiency of the technologies.
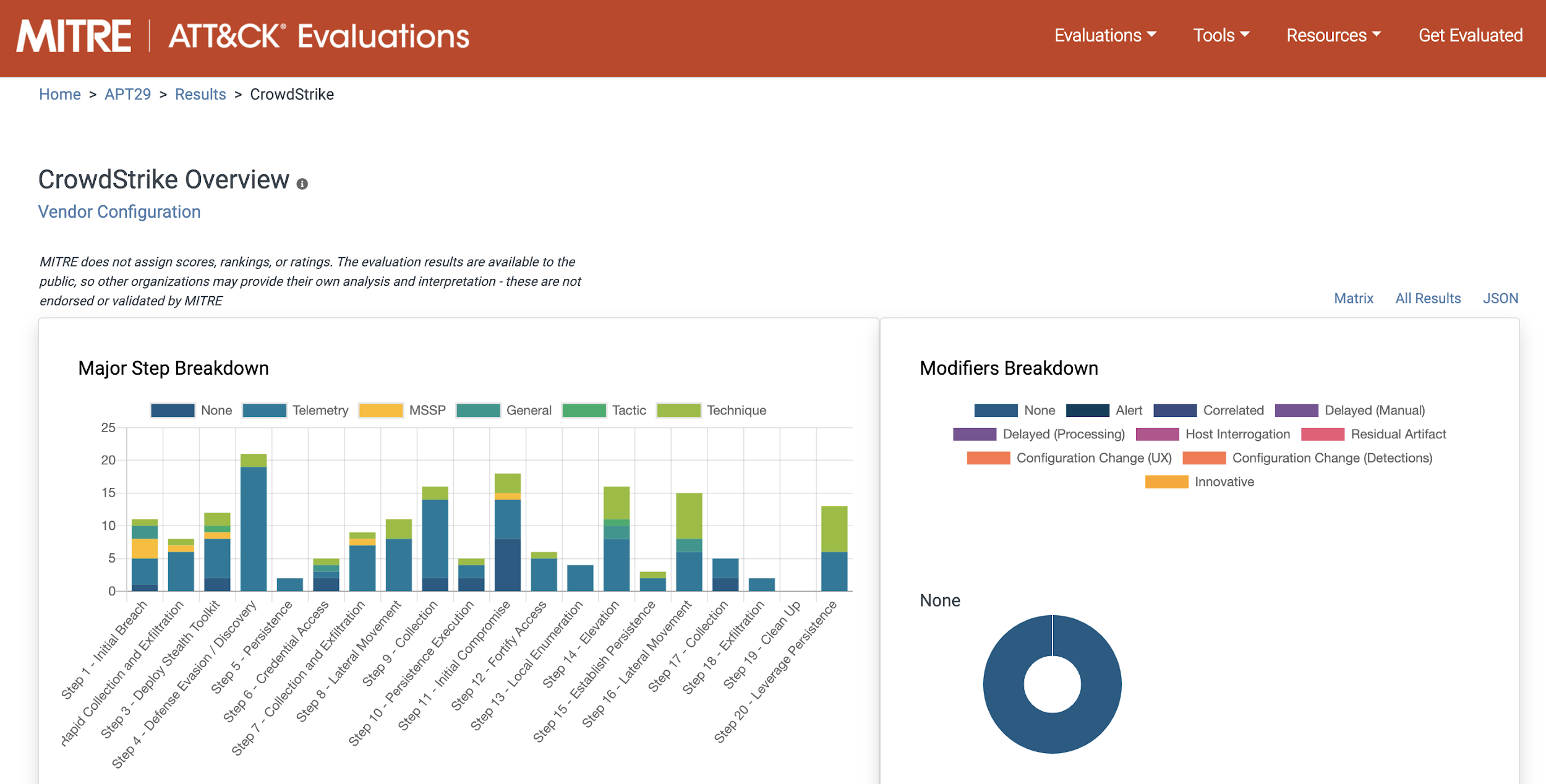
Figura 7: Evaluación de Falcon de MITRE ATT&CK
https://attackevals.mitre.org/APT29/results/crowdstrike/
Conclusion
The purpose of automating the attacker emulation is to have a standardized set of tests that allows us to be evaluating within our environment on a recurring basis the tactics and techniques commonly used by Adversaries for different types of attacks, and to optimize the tests of our Red Team by having an easy to create environment and easy to replicate tests on the assets of our organization, in addition to helping our Blue Team for refining the detection based on the monitoring of the evidence of the tests, all this to meet the cycle of Prevention, Detection and Response in an Automated way.
It is important to mention that despite the MITRE ATT&CK detection evaluations that can help us to make a decision when acquiring a security product, we cannot rely solely on this criterion, since in the security environment every day vulnerabilities, tactics and techniques are discovered and it is necessary to be aware and checking their applicability in our environments, that is why it is so important to have an adversary emulation automation scheme that allows us to be up to date and mitigate the risk as much as possible in the shortest time.
Splunk Phantom + Atomic Red Team + Falcon Crowdstrike









