In the last few weeks we have been facing a new global pandemic, there have been some before, the last one was H1N1 in 2009 where many companies began to create their business continuity plans and began the scenarios where you considered a viral outbreak as a threat to the business and operations on site, how are or were these continuity plans built? well now we are seeing/proving it.
There are European countries where they have already launched their remote work processes, right now America is starting to escalate the emergency levels and they are starting the Virtual events modality and meetings via teleconference.
From the user's perspective, do you know the basic guidelines that you should consider in order to work safely from home? SANS has created a small guide with 5 simple steps to consider, it is important what one should consider if you are a user, who due to contingency plans has had to stay at home to work.
And from a corporate perspective
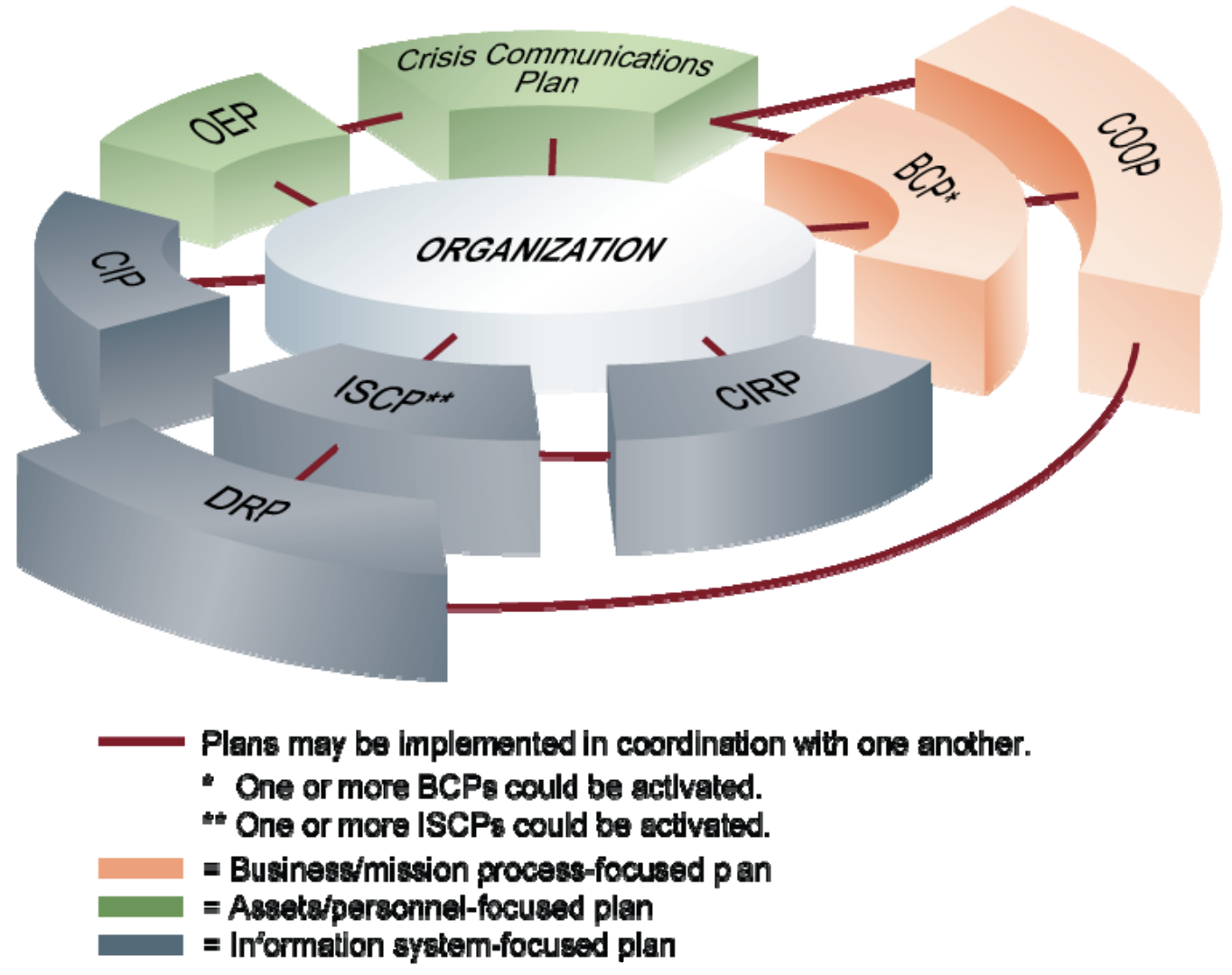
Do you know when to start your continuity plan, what types of plans do you have in place? According to SANS the activation conditions of a BCP (Business Continuity Plan) are triggered when a given incident threatens the mission of the operations.
The threats may include threats to people, to the facilities and to the environment, which require emergency response action. Threats to critical infrastructure essential to the operation of the organizations (facilities, power, water supplies, or communication networks), threats to critical supply chain operations.
The Emergency Manager declares the activation of a BCP in order to initiate the recovery process of services and communications. The activation of the BCP puts into action the contingency operations starting with the critical services and processes.
There are 8 different types of plans according to NIST, depending on the threat, event or situation that arises.
%2010.08.24.png?width=800&name=Captura%20de%20Pantalla%202020-03-15%20a%20la(s)%2010.08.24.png)
And in all these processes and plans that you have documented, and how well are your security KPIs, the companies that offer you traditional SOC services will also begin to work remotely, are they adapted to this modality of work or will the service be diminished? It is interesting how right now working with cloud services, remote work models, collaborative platforms and agile work models are becoming very important. If you want to implement them, we can help you.
IT security for remote work
Let's look at security, surely within the IT security strategy for the remote work that you are considering:
- VPN for internal and external collaborators.
- Mobile equipment with anti-malware systems that do not depend on the corporate network.
- Access consolidation systems or remote privileged access.
- Software repositories accessible from the outside.
- Encrypted communication systems.
- Monitoring systems that adapt to hybrid infrastructures.
- Within all these actions we surely have controlled/monitored the ABC (Additions, Deletions, Changes) of our systems and applications.
Within all these actions we surely have controlled/monitored the ABC (Additions, Deletions, Changes) of our systems and applications.

We have KPIs on
- How many providers are connected via VPN
- From which locations they are accessing
- Our remote users are connected to the networks they should be connected to.
- Assigned passwords are being used appropriately
- Work/changes made are being reported in a collaborative manner (how long, which systems?)
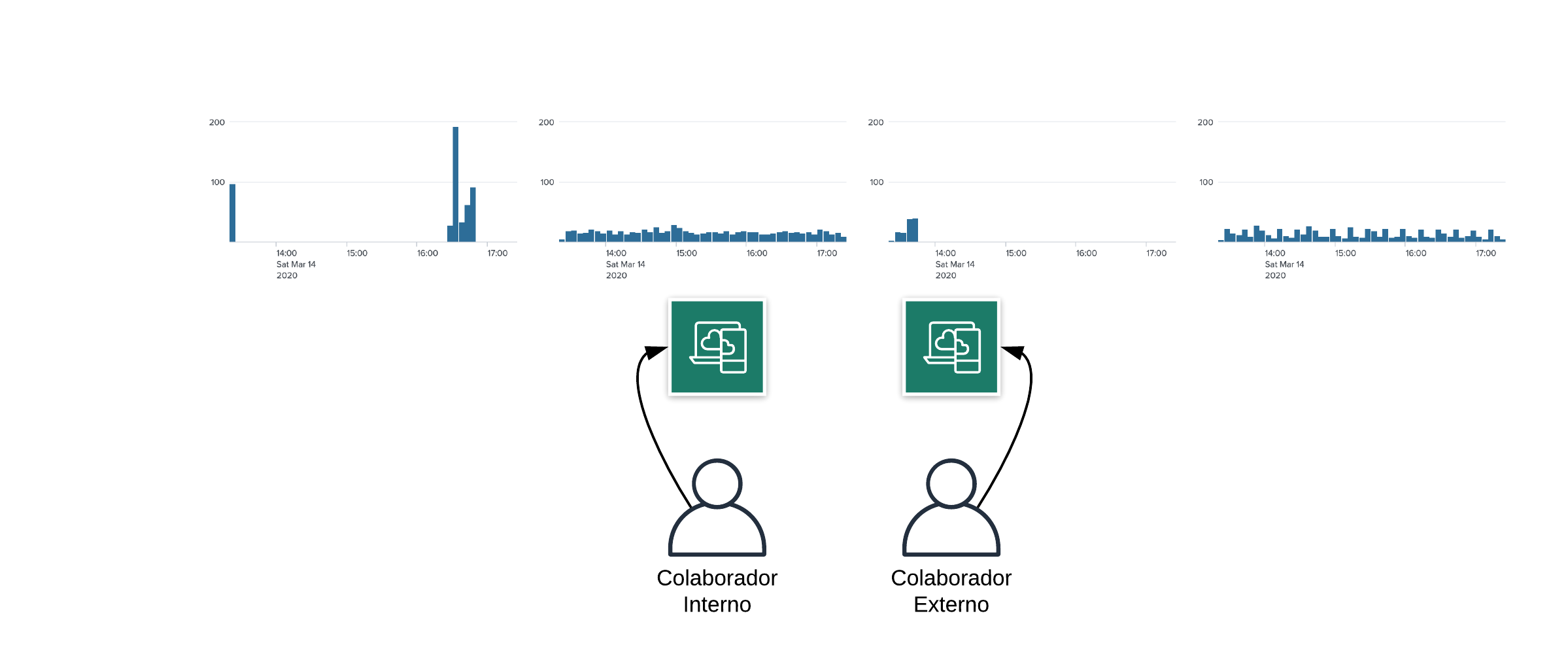
These indicators reflect the need to understand my level of security regarding access to the organization's information.
We must consider that these situations are eventual and we are not necessarily prepared for all the risks that could exist and we must be prepared to work efficiently and securely
Some recommended settings for these situations
If the strategy already has a VPN and your communication systems such as Email or Corporate Chat are accessible remotely, have you considered two-factor authentication?
You have the control panels so that there are no users outside the authorized geography or the volume of access is abnormal.
It is normal not to have all the corporate equipment for the personnel, surely some people will use personal equipment, we should consider EDR (Endpoint Detection and Response) systems for their protection and we should also be aware of what happens in the communications towards the corporate infrastructures.
The different administrators of the organization should be receiving reports of relevant information that could be these KPIs with visual panels, in which we can identify unauthorized activities and be able to act accordingly in a remote, fast and effective way.
Something that could happen in these circumstances is that in the event of a security problem we need to restart some equipment or we need to move to the data centers. Have our automation tools been tested enough so that in a situation like this we can continue to manage it remotely?
Finally, it is important to learn from these global scenarios where our life and the way we work can change, this learning will lead us to be more efficient organizations and therefore more secure, technologies exist, methodologies also exist, integrating the best capabilities in the environments in a fast way is one of the challenges we are currently facing.
A3Sec is an organization that was born in the decentralized models of security, communication and remote work, we understand the risks that exist and we support the different organizations to obtain the necessary visibility to understand the security of the organizations.
Do you need to protect your communications and data in today's remote work environment?