It is estimated that cybersecurity breaches take more than 280 days to be identified and managed by organizations, which challenges technology teams to adopt a more comprehensive strategy to block layered attacks before they impact critical information, according to A3Sec.
In a scenario of high diversification of cyber attacks today, the multinational A3Sec appeals to the unified operation of cybersecurity to meet the current challenges in the field and avoid losses equivalent to about US$4 million for an incident of this type on average for organizations.
Adopting a proactive, layered strategy will allow organizations to shield their critical information against cybercrime, given that "potential Internet risks can occur at multiple levels," according to the U.S. firm IBM.
Incidentally, a report released last December by Cisco warns that 39% of the security technologies used by companies are considered obsolete and highlights that organizations that: "proactively test their security capabilities are 2.5 times more likely to maintain business resilience", something it concluded after conducting a survey of more than 5,100 security and privacy professionals in 27 countries.
Layered cybersecurity provides support for organizations at different levels, ranging from basic system security to network protection to prevent unauthorized access through common tools such as so-called firewalls.
IBM explains that "the network security scheme should indicate what security measures the ISP provides, such as ISP router connection filtering rules and public domain name system (DNS) precautions."
Layer-based cybersecurity also addresses other levels of shielding, including the use of applications and services that may be vulnerable to user malpractice, as well as transmission-level security, which relates to protecting the flow of data between different networks in organizations.
Having a single shield against IT attacks is not enough because it does not guarantee security against all possible IT risks. On the other hand, the combination of tools or specialized services does enhance the levels of protection.
Thus, the layered security system seeks to prepare all areas of the company for possible attacks. In this way, protection is more complete and defense is much more proactive.
Inaction is costing businesses
These security schemes are key to companies' finances at a time when cloud and operations control networks have changed the dynamics of business in the era of the internet of things, with more than 10 billion devices connected to each other that manage sensitive information.
Moreover, the rapid adoption of hybrid cloud in the corporate world to facilitate remote tasks is having a positive effect on their competitiveness, but at the same time "the complexity of the infrastructure is creating vulnerabilities that cybercriminals are exploiting to perpetrate attacks," according to a report by the IBM Institute for Business Value (IBV) in collaboration with Oxford Economics.
Worryingly, "more than a third of global respondents surveyed indicated that improving cybersecurity and reducing risk is not part of their major business and IT investments", but 80% were aware that "data security integrated into the entire cloud architecture is important or extremely important".
Information shared at a recent A3Sec event indicates that companies today face significant gaps in managing security vulnerabilities and often take action too late, in which time attackers manage to penetrate different levels of organizations and put even their operations at risk.
At this point it is worth remembering the attack suffered by the extensive Colonial Pipeline, located in Alpharetta (Georgia), by cybercriminals who carried out a malicious campaign between May 6 and 7 last year.
This infrastructure was the victim of malware that not only paralyzed its operations, but also put the U.S. oil industry at risk to the point that President Joe Biden had to declare a state of emergency.
This case is reflective of many companies that currently manage critical data, but have fragile policies to deal with these events. In fact, A3Sec shared that on average organizations do not have the capacity to analyze more than 80% of the information considered key to manage cybersecurity in their processes.
Keys to managing cybersecurity in the organizations
A3Sec proposes several keys to manage cybersecurity at a new competitive level and as a first step says that it is necessary to develop the ability to generate and continuously update an inventory of assets, which consists of identifying what must be protected and which are the critical assets of the business.
Once this task is done, it is important to define a position on cybersecurity in order to have a continuous management, as well as to monitor the evolution of these processes and adopt safe habits for the detection of anomalies.
On the other hand, it is important to adopt cybersecurity intelligence management to provide a context for new threats that may affect companies, always staying one step ahead of cyberattackers with tools such as artificial intelligence or data analysis.
On this topic, the Cisco Security study indicates that companies with integrated technologies are seven times more likely to achieve high levels of process automation. In addition, these organizations have a threat detection capability that is more than 40% stronger.
A3Sec specialists also invite to develop capabilities to detect and react effectively to the unknown, while defining a health monitoring and service levels of the organization's value chain.
Finally, A3Sec sees it as important to take firm steps in terms of hyper-automation, which consists of generating operational efficiencies of the cybersecurity management model through orchestration and task automation capabilities.
A strategy that is complemented by the search for continuous improvement through periodic evaluations of the effectiveness of security controls to identify opportunities for savings and efficiency in their operation.
A3Sec solutions include detection capabilities in hybrid Cloud, IT, OT and IoT OnPremise networks and analytics services to prevent cyber threats to data confidentiality or anomaly detection tools, which work with a statistical and deterministic system for greater accuracy.
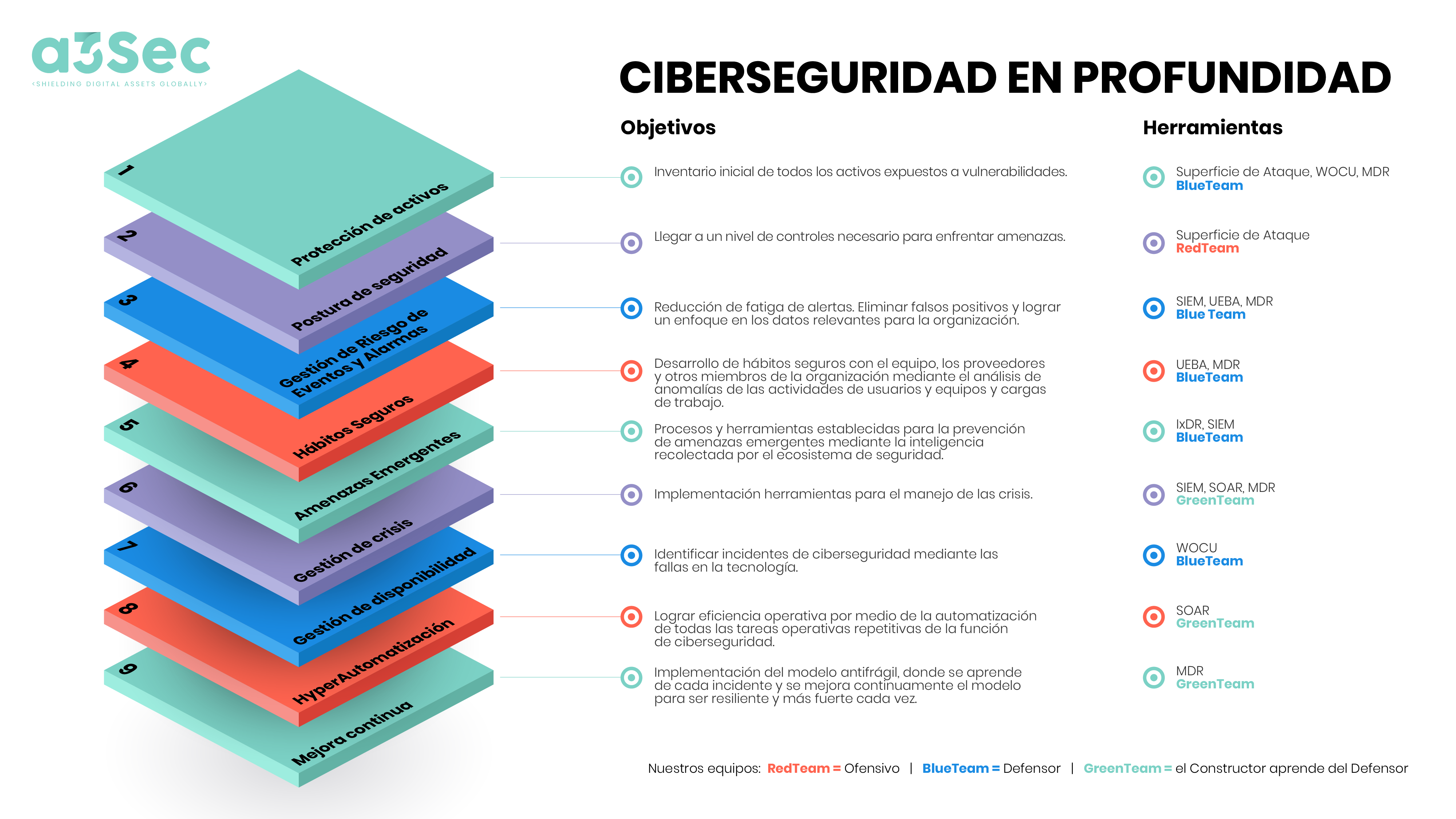
With the layered system for security, it guarantees protection against new threats, while helping to comply with regulations, generating a much more efficient service and offering improvements in the user experience.









