
Security Operations Center (SOC) Its Evolution
29 November, 2023
See everything

29 November, 2023
28 November, 2023

29 June, 2023

20 January, 2023

20 January, 2023

20 January, 2023

05 January, 2023

05 January, 2023

05 January, 2023

05 January, 2023

05 January, 2023

02 January, 2023

29 December, 2022

29 December, 2022
29 December, 2022
29 December, 2022

12 December, 2022

12 December, 2022

12 December, 2022

07 December, 2022

06 December, 2022

06 December, 2022

18 November, 2022

18 November, 2022

14 October, 2022

14 October, 2022

14 October, 2022

14 October, 2022
14 October, 2022

14 October, 2022

14 October, 2022

14 October, 2022

14 October, 2022
09 September, 2022
09 September, 2022

09 September, 2022
26 August, 2022
26 August, 2022
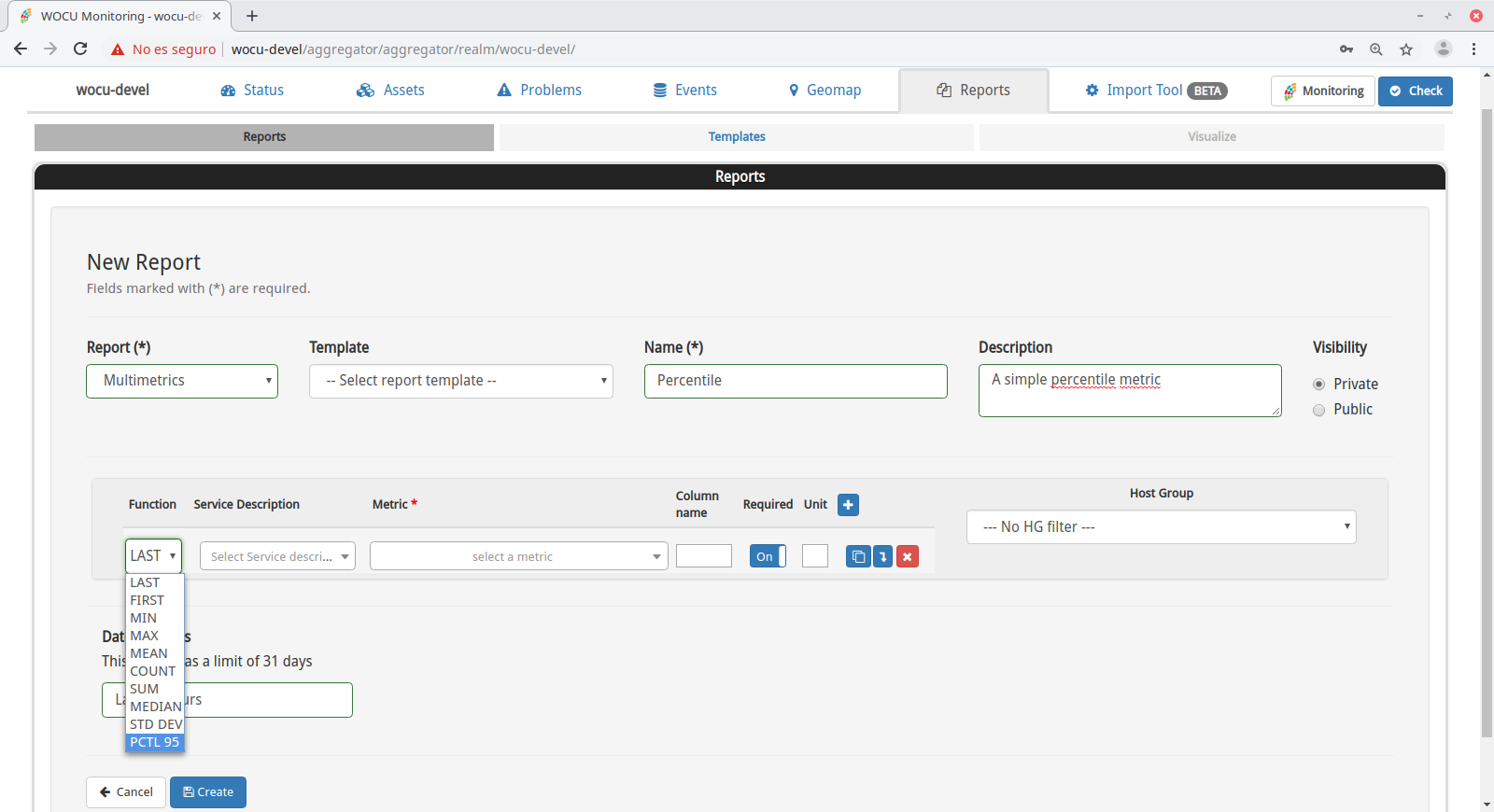
26 August, 2022

26 August, 2022

26 August, 2022
19 August, 2022

19 August, 2022

19 August, 2022
19 August, 2022
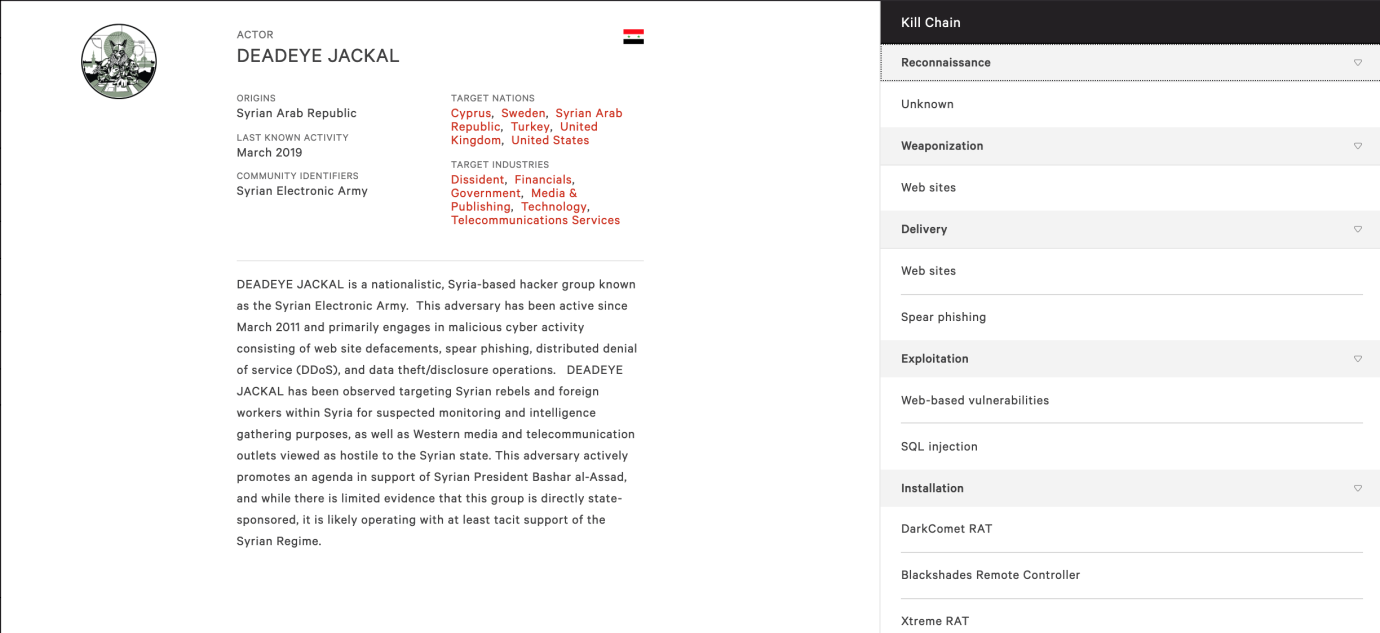
19 August, 2022

19 August, 2022

19 August, 2022

11 August, 2022
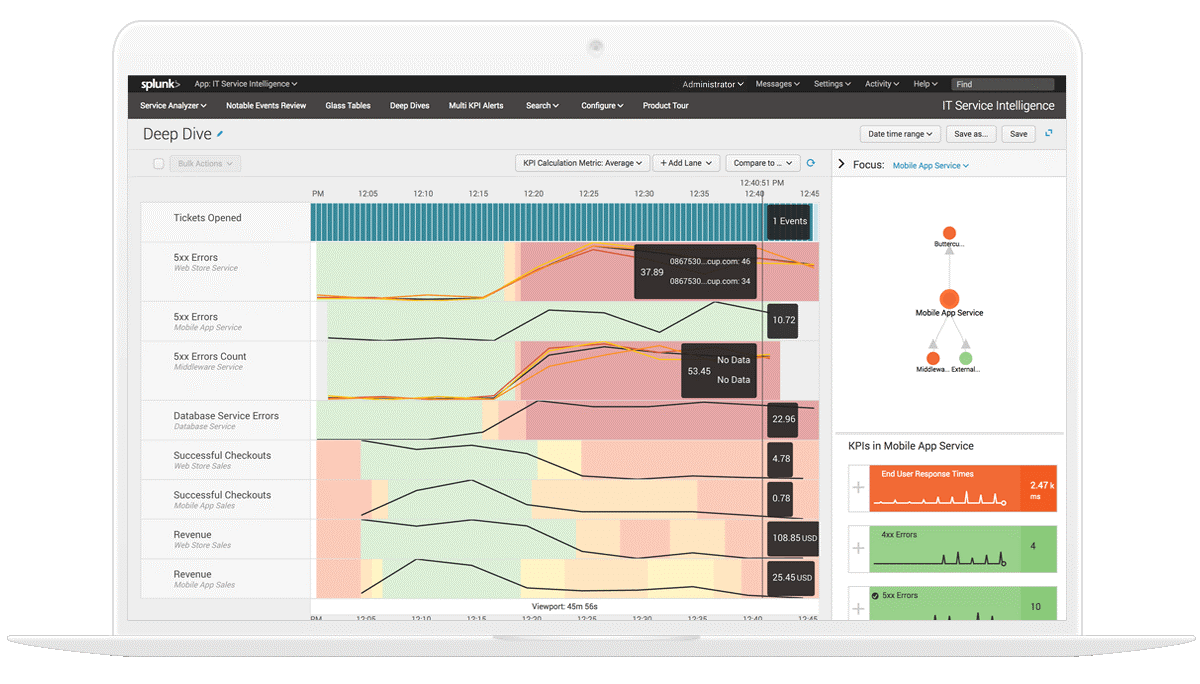
11 August, 2022
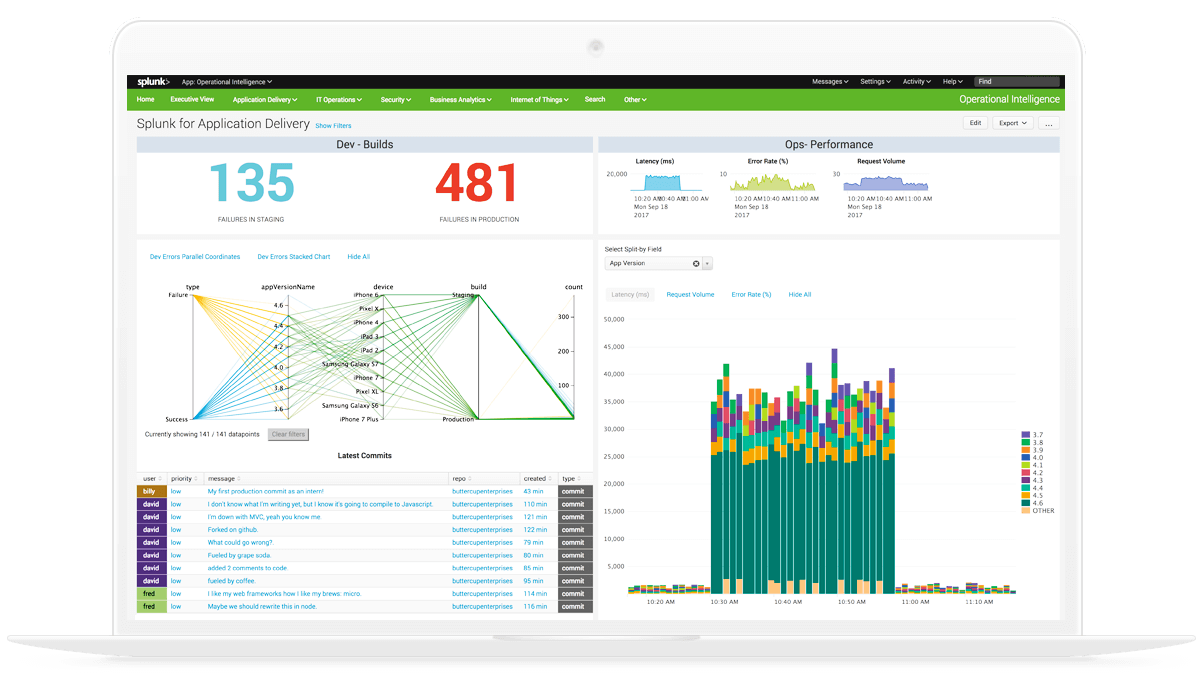
11 August, 2022

11 August, 2022
11 August, 2022

11 August, 2022

11 August, 2022

11 August, 2022

11 August, 2022

11 August, 2022

11 August, 2022
11 August, 2022
11 August, 2022
11 August, 2022

11 August, 2022
11 August, 2022

11 August, 2022

11 August, 2022

11 August, 2022

11 August, 2022
11 August, 2022

11 August, 2022

11 August, 2022

11 August, 2022
11 August, 2022

11 August, 2022

10 August, 2022

10 August, 2022

10 August, 2022
10 August, 2022
10 August, 2022
10 August, 2022

10 August, 2022

10 August, 2022
10 August, 2022

10 August, 2022

10 August, 2022

10 August, 2022

10 August, 2022

10 August, 2022

10 August, 2022

10 August, 2022

10 August, 2022

10 August, 2022

10 August, 2022

10 August, 2022
10 August, 2022

10 August, 2022

10 August, 2022

10 August, 2022

10 August, 2022

10 August, 2022

10 August, 2022
10 August, 2022

10 August, 2022

10 August, 2022

10 August, 2022

10 August, 2022

10 August, 2022

10 August, 2022
10 August, 2022